Navigating the Torrent Landscape: A Guide to Safe and Secure Downloads
Related Articles: Navigating the Torrent Landscape: A Guide to Safe and Secure Downloads
Introduction
With great pleasure, we will explore the intriguing topic related to Navigating the Torrent Landscape: A Guide to Safe and Secure Downloads. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Torrent Landscape: A Guide to Safe and Secure Downloads

The world of torrents has long been associated with a certain level of risk, a perception fueled by concerns about malware, copyright infringement, and privacy breaches. However, with careful navigation and a robust understanding of the inherent risks, downloading torrents can be a safe and efficient method for accessing a vast library of digital content. This article delves into the intricacies of safe torrenting, providing a comprehensive guide for users seeking to harness the power of this technology without compromising their security.
Understanding the Torrent Ecosystem
Torrents, or peer-to-peer (P2P) file sharing, operate on a decentralized network where users contribute to and receive data from each other. This eliminates the need for centralized servers, enabling efficient distribution of large files. However, this decentralized nature also presents challenges in terms of security and trust.
The Risks Associated with Torrent Downloads
- Malware: Malicious software disguised as legitimate files is a common threat within torrent ecosystems. These files can infect systems with viruses, spyware, ransomware, and other harmful programs.
- Copyright Infringement: Downloading copyrighted material without authorization is illegal and can result in legal repercussions, including fines and prosecution.
- Privacy Concerns: Torrenting exposes your IP address and other personal information to other users on the network, making you vulnerable to monitoring and potential identity theft.
- Unreliable Sources: The decentralized nature of torrents means that file authenticity and integrity cannot be guaranteed. Downloads from untrusted sources may be corrupted, incomplete, or contain malicious content.
Strategies for Safe Torrenting
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet traffic and masks your IP address, safeguarding your privacy and anonymity. Choosing a reputable VPN provider with a strong no-logs policy is crucial.
- Download from Trusted Sources: Opt for reputable torrent sites with a history of providing verified and secure files. Check user reviews and ratings to gauge the trustworthiness of a source.
- Employ a Torrent Client with Security Features: Select a torrent client that offers built-in security features such as malware scanning, file integrity verification, and anti-virus protection.
- Verify File Integrity: Before opening any downloaded torrent file, use a checksum tool to verify its integrity. This ensures that the file has not been tampered with during the download process.
- Stay Updated: Maintain your operating system and security software with the latest updates to protect against emerging threats.
- Be Aware of File Extensions: Exercise caution with unfamiliar file extensions and avoid downloading files from sources that seem suspicious.
Choosing the Right Torrent Client
Several torrent clients offer a range of features and security measures. Popular options include:
- qBittorrent: Open-source, feature-rich, and highly regarded for its security and privacy focus.
- uTorrent: A popular and lightweight client, but its security features have been questioned in the past.
- Deluge: A versatile client with a focus on flexibility and customization.
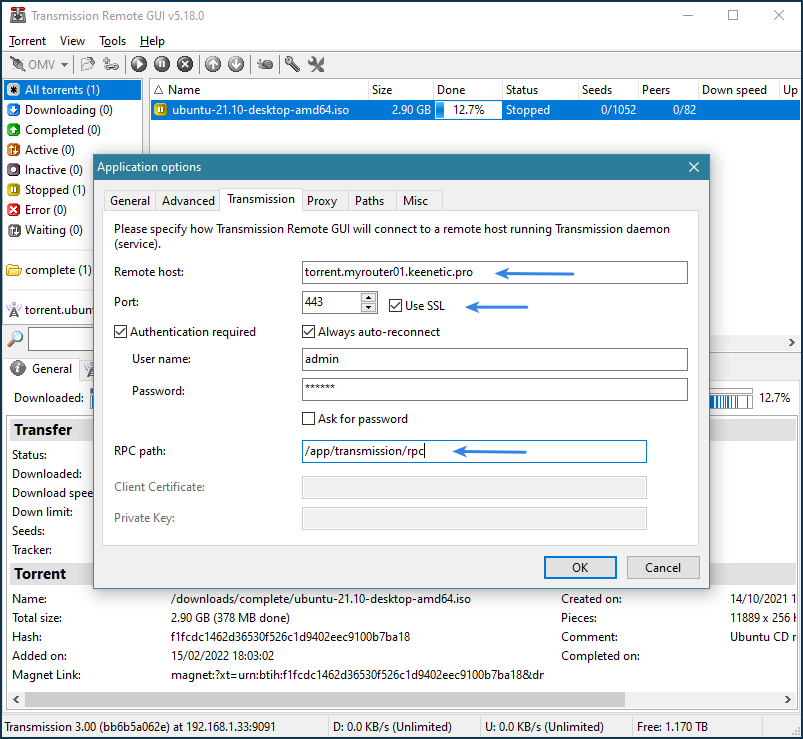
- Transmission: A lightweight and minimalist client known for its simplicity and efficiency.
FAQs about Safe Torrenting
Q: Are all torrents illegal?
A: No, not all torrents are illegal. While downloading copyrighted material without authorization is illegal, torrents are a legitimate tool for sharing public domain content, open-source software, and other legal files.
Q: Is it safe to download torrents from public trackers?
A: Public trackers are more prone to malware and copyright infringement issues. Opting for private trackers, which require membership and often have stricter moderation policies, can enhance security.
Q: Can I use a VPN to completely anonymize my torrent activity?
A: While a VPN significantly enhances privacy, it cannot guarantee complete anonymity. Other factors, such as your ISP’s logging practices and the specific VPN provider’s security measures, can influence your level of anonymity.
Q: What are the best practices for torrenting copyrighted content?
A: Downloading copyrighted material without authorization is illegal. It is crucial to respect intellectual property rights and obtain legal access to content through authorized channels.
Tips for Safe Torrenting
- Use a strong password for your torrent client and avoid sharing it with others.
- Be cautious about opening downloaded files before verifying their integrity.
- Regularly scan your system for malware and keep your security software updated.
- Consider using a dedicated computer for torrenting to minimize the risk of infecting your primary system.
Conclusion
While torrenting can be a powerful tool for accessing a vast library of digital content, it requires a cautious approach to mitigate the inherent risks. By understanding the potential threats, employing robust security measures, and downloading from reputable sources, users can navigate the torrent landscape safely and securely. Remember, responsible torrenting involves respecting intellectual property rights, prioritizing privacy, and staying vigilant against malicious software.





Closure
Thus, we hope this article has provided valuable insights into Navigating the Torrent Landscape: A Guide to Safe and Secure Downloads. We appreciate your attention to our article. See you in our next article!